Collectors Universe
Verified in Real Time

The market for numismatics – the collecting of rare coins – is estimated to exceed $3 billion.
Collectors Universe uses HID's Trusted Tag Services to prove the authenticity of products and to verify the information on the tag. Collectors and dealers can verify PCGS-sealed coins in real time. Trusted NFC tags are embedded in coin holders with discrete inlays that are not visible behind the PCGS label. The collector touches the coin holder with an NFC-enabled smartphone and can then authenticate the collectible via the Cloud Authentication Service.
Each "tap" generates a unique cryptographically distinct URL that automatically launches Collectors Universe's proprietary PCGS Cert Verification App or opens a web browser to display information about the authenticity of the coin or banknote. The website also displays more in-depth information such as inventory reports, estimated value and high-resolution images.
Because a unique URL is generated with each "tap", the information cannot be cloned or manipulated.
The Rollout of Two Million NFC Tags
The cryptography of Trusted NFC tags and easy verification via smartphone allows for convenient handling. This service provided for PCGS and Collectors Universe products generates trust and increases buyer confidence. The customer has assurance that their investment is a certified collectible and not a counterfeit.
Collectors Universe initially rolled out the solution on approximately 100,000 coins to test compatibility and customer response. Following the successful pilot, two million more Trusted NFC tags are now in use to incorporate the extensive inventory of encapsulated coins, medals, tokens and banknotes.
Collectors Universe uses HID's Trusted Tag Services to prove the authenticity of products and to verify the information on the tag. Collectors and dealers can verify PCGS-sealed coins in real time. Trusted NFC tags are embedded in coin holders with discrete inlays that are not visible behind the PCGS label. The collector touches the coin holder with an NFC-enabled smartphone and can then authenticate the collectible via the Cloud Authentication Service.
Each "tap" generates a unique cryptographically distinct URL that automatically launches Collectors Universe's proprietary PCGS Cert Verification App or opens a web browser to display information about the authenticity of the coin or banknote. The website also displays more in-depth information such as inventory reports, estimated value and high-resolution images.
Because a unique URL is generated with each "tap", the information cannot be cloned or manipulated.
The Rollout of Two Million NFC Tags
The cryptography of Trusted NFC tags and easy verification via smartphone allows for convenient handling. This service provided for PCGS and Collectors Universe products generates trust and increases buyer confidence. The customer has assurance that their investment is a certified collectible and not a counterfeit.
Collectors Universe initially rolled out the solution on approximately 100,000 coins to test compatibility and customer response. Following the successful pilot, two million more Trusted NFC tags are now in use to incorporate the extensive inventory of encapsulated coins, medals, tokens and banknotes.

The market for numismatics – the collecting of rare coins – is estimated to exceed $3 billion.
“We want collectors to be confident that when they have PCGS-authenticated, graded, and encapsulated coins and banknotes in their hands, they are holding an authentic and valuable collector’s item.”

NFC-Tags and Cloud-Based Authentication
Cloud-Based Solution: Trusted Tag Services
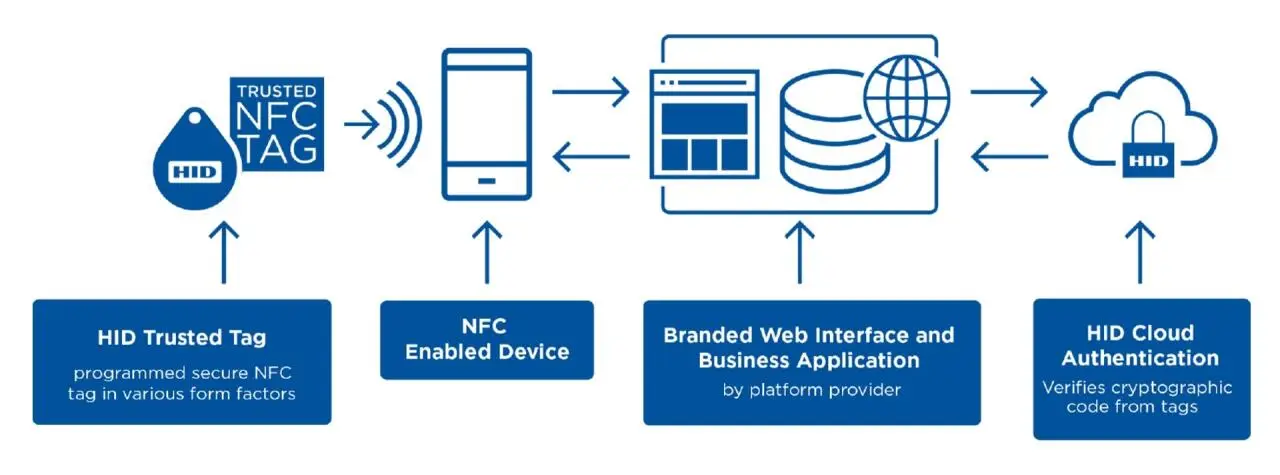
HID Trusted Tag Services facilitates transactions by tapping an attached or embedded NFC tag with an NFC-enabled smartphone or tablet. Information is communicated securely. The solution ensures seamless authentication suitable for a wide range of powerful and dynamic applications.
No additional readers are required for deployment. The Trusted Tags are available in a variety of form factors and can be attached to or embedded in virtually any object. The platform also provides data analytics on every transaction. In-depth insights into consumer behavior are identified.
Data read from NFC tags has additional security and privacy attributes that change with each "tap," making counterfeiting attempts impossible. For HID Trusted Tag Services, the trusted NFC tags are combined with a cloud-based authentication platform. The result: unique and trustworthy identities.
Unique Cryptographic Code
Each time a Trusted NFC tag is "tapped," the NFC-enabled smartphone receives a URL with a unique cryptographic code. The tag generates this code at the moment of the tap. The web server that manages the user environment then determines whether the URL was accessed by someone who physically tapped on a tag or whether a shared web link was followed or if the URL was entered manually.
This cryptographic feature prevents a URL from being used multiple times without physical touch and makes it impossible to clone the tag.
If the URL is not accessed by a validated physical "tap", the transaction can be denied by the server or simply logged for later analysis.
If the location of the tag is known, each valid "tap" indicates proof of presence at the time of the "tap".
"HID Trusted Tag Services is ideal for providing trusted and tamperproof identities for collectibles that have gone through the PCGS verification process. Containers that are tamper-proof and sealed via ultrasonic welding contain the coin plate and NFC tag. Verification of the NFC tag allows for very simple and secure validation of the coin's authenticity, which is affixed on the coin plate through an encapsulation process. We are pleased to be working with PCGS on this deployment."

While a QR code can be copied very quickly, each "tap" generates a unique cryptographically distinct URL. The information cannot be cloned or manipulated.
"Collectors Universe is the first company in the numismatic collectibles field to technologically secure counterfeit protection on a large scale with HID Trusted Tag Services. Ensuring the authenticity, certification and grading of collectibles is crucial."

Trusted Tags for Identification, Authentication and Verification
Originality and Customer Trust

Collectors Universe uses Trusted NFC tags to provide customers with the means to prove the authenticity of products in real time via the cloud, and to verify the information on the label.
Collectors Universe uses Trusted NFC tags to provide customers with the means to prove the authenticity of products in real time via the cloud, and to verify the information on the label.

Counterfeit and Quality Protection

Old Kempton Distillery whiskeys are produced on-site, then distilled, aged and bottled all on their property. A cryptographically secure HID Trusted Near Field Communication (NFC) tag is embedded into the label of every liquor bottle, which links to HID’s cloud authentication service.
Old Kempton Distillery whiskeys are produced on-site, then distilled, aged and bottled all on their property. A cryptographically secure HID Trusted Near Field Communication (NFC) tag is embedded into the label of every liquor bottle, which links to HID’s cloud authentication service.

Security and Maintenance

Fire protection is a tall order at one of lower Manhattan’s most iconic office buildings, requiring regular inspection and maintenance of its massive, sprawling industrial sprinkler system.
Fire protection is a tall order at one of lower Manhattan’s most iconic office buildings, requiring regular inspection and maintenance of its massive, sprawling industrial sprinkler system.

Originality and Brand Protection

Prevent counterfeiting and warranty fraud while also engaging with the consumer.
Prevent counterfeiting and warranty fraud while also engaging with the consumer.

Identification and Proof of Presence

Nearly 430 million patient visits occur in the U.S. each year. Each of these visits must be documented in terms of content and time.
Nearly 430 million patient visits occur in the U.S. each year. Each of these visits must be documented in terms of content and time.

Customer Service and Speed

By just holding a smartphone on a pop device for a few seconds, a user is instantaneously offered a new universe of digital services tailored and related to the pop location / table in the restaurant.
By just holding a smartphone on a pop device for a few seconds, a user is instantaneously offered a new universe of digital services tailored and related to the pop location / table in the restaurant.

Interview with Mark Robinton and Rahul Kothari
NFC Tags Conquer New Business Fields

Mark Robinton: VP IoT Services BU, Identification Technologies, HID Global on the left, and Rahul Kothari: Sales Director, Trusted Tag Services, HID Global on the right.
In this interview, Mark Robinton and Rahul Kothari explain the benefits for end users, which applications the solution is designed for, and what makes the solution so special.
In this interview, Mark Robinton and Rahul Kothari explain the benefits for end users, which applications the solution is designed for, and what makes the solution so special.

Mark Robinton: VP IoT Services BU, Identification Technologies, HID Global on the left, and Rahul Kothari: Sales Director, Trusted Tag Services, HID Global on the right.
Interview
1. What is the objective of Trusted Tag Services?
Robinton: The ultimate goal is to provide an authentication solution that is easy and convenient for the end user, and to provide a pleasant user experience. The verification processes run in the background, virtually automated – seamless to customer. All the user has to do is "tap" an NFC-enabled smartphone to the object. When a "tap" is made, either a green checkmark or a red "X" appears.
The one-time authentication via the cloud cannot be copied and cloned. As a result, one gains security without having to compromise on convenience. The solution also offers a wide range of form factors and thus a high degree of flexibility. Another important factor in times of global chip shortages is that HID Global is technology agnostic in terms of specific chip suppliers. So if the chip must be replaced due to supply chain issues or cost, authentication is carried out using the same principle. An app or other software is also not required. As such, the Trusted Tag concept offers simplicity, security and convenience at the same time.
2. In which application scenarios can the Trusted Tag simplify and secure processes?
Robinton: We focus on three main categories. First, on digital proof of presence, which can be used in the medical field to document and prove that caregivers are definitely present in a patient's home.
Second, the Trusted NFC tag provides proof of identity. This can be, for example, the employee ID card, which enables access controls and proof of authorization. One application is the documentation of personnel and their work authorization on large construction sites.
Thirdly, there is counterfeit protection. The genuineness of a product can be immediately authenticated and verified with Trusted NFC tags. If a customer purchases an original product with this verification, they can use it for resale to prove authenticity with the tag history. There is no need for renewed verification by an expert.
3. Let's stay with the example of product authentication.
Kothari: The market for collectibles is a rapidly growing market. There is a huge demand for coins, baseball cards or video games. Two examples: Older "Super Mario" video games are trading for around $200,000 and "The Legend of Zelda" was recently acquired for $187,000. In the sports sector, jerseys or signed autographs are also very much in trend. Sneakers, such as Air Jordans, are also very popular.
4. How does the solution work for valuable collectibles?
Kothari: The Trusted Tag solution is used to authenticate these products in real time. Collectors Universe uses Trusted NFC tags to prove the authenticity of the products and to verify the information on the label. Collectors and dealers can thus verify PCGS-sealed coins in real time. The Trusted NFC tags are embedded in the coins and holders with discrete inlays that are not visible behind the PCGS labeling. The collector taps the coin holder with an NFC-enabled smartphone to authenticate the collectible via the Cloud Authentication Service.
Each tap generates a unique cryptographic one of a kind URL that automatically launches Collectors Universe's proprietary PCGS Cert Verification App or opens a web browser to display information about the authenticity of the coin or banknote.
5. What benefits does the end user receive from Trusted NFC tags?
Kothari: The user or customer does not have to install an app, but instead receives the information automatically via a "tap". The biggest advantage is the unique authentication via the cloud, which cannot be copied. While a QR code can be copied very quickly, each "tap" generates a unique cryptographically distinct URL.
The information cannot be cloned or manipulated. The second aspect is the tremendous flexibility offered by the variety of form factors. These include key fobs, stickers, labels, smart cards, inlays, coins and hard tags.
Robinton: In addition, the security application of the product itself is exciting. Security is built in "invisibly" without much effort on the part of the end user. In many security aspects today, multi-factor authentication is used. For example, a user enters a password and then receives the required code. So the time for the log-in process is extended.
One of the key advantages of the Trusted NFC tag solution is that we do not add any additional burden to this interaction. Whether the QR code is scanned or the NFC tag or Trusted Tag is read, the smartphone is tapped and the interaction started. Nothing else has to be done, because the security feature has already been built in behind the scenes, so to speak.
6. How do you see this impacting the buyer's journey?
Kothari: If a company can offer a genuine experience with a product, then the entire sales experience for the customer is optimized and sales transactions are stimulated. The brand and the customer come into direct contact, so to speak, which is far more than just sealing a deal. The customer is given the opportunity to return to the product and use it again. For example, in the form of a discount promotion for the next product that is launched or an exclusive invitation to an event. This gives companies a direct connection to the end consumer.
7. Many companies are currently affected by supply chain restrictions and chip shortages. Is HID Global also affected by this?
Robinton: HID Global is independent of chip vendors. We support chips from a wide variety of vendors. This means that if a chip is unavailable due to supply chain issues or cost, another can be easily substituted. Authentication is done through the same principle and service. The fact that we are not tied to a specific provider is a key advantage for customers.






-über-Wi-Fi-HaLow-responsive.webp)
